Quantum cryptography uses physics to develop a cryptosystem completely secure against being compromised without knowledge of the sender or the receiver of the messages. The word quantum itself refers to the most fundamental behavior of the smallest particles of matter and energy.
Quantum cryptography is different from traditional cryptographic systems in that it relies more on physics, rather than mathematics, as a key aspect of its security model.
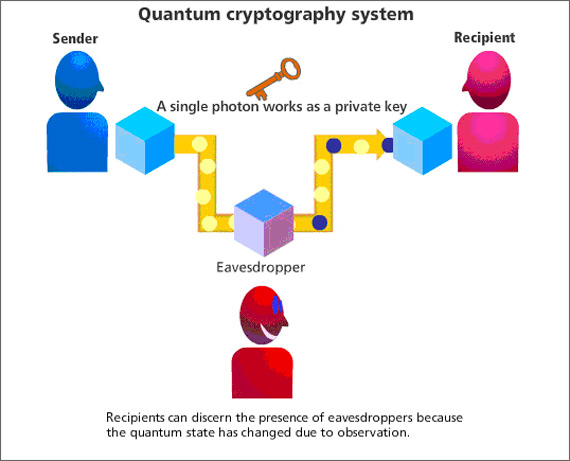
Essentially, quantum cryptography is based on the usage of individual particles/waves of light (photon) and their intrinsic quantum properties to develop an unbreakable cryptosystem (because it is impossible to measure the quantum state of any system without disturbing that system.)
Quantum cryptography uses photons to transmit a key. Once the key is transmitted, coding and encoding using the normal secret-key method can take place. But how does a photon become a key? How do you attach information to a photon’s spin?
This is where binary code comes into play. Each type of a photon’s spin represents one piece of information -usually a 1 or a 0, for binary code. This code uses strings of ones and zeros to create a coherent message. For example, 11100100110 could correspond with “h-e-l-l-o”. So a binary code can be assigned to each photon, for example, a photon that has a vertical spin ( | ) can be assigned a 1.
“If you build it correctly, no hacker can hack the system. The question is what it means to build it correctly”, Renato Renner, the Institute of Theoretical Physics in Zurich.
Regular, non-quantum encryption can work in a variety of ways but generally a message is scrambled and can only be unscrambled using a secret key. The trick is to make sure that whomever you’re trying to hide your communication from doesn’t get their hands on your secret key. Cracking the private key in a modern crypto system would generally require figuring out the factors of a number that is the product of two insanely huge prime numbers. The numbers are chosen to be so large that, with the given processing power of computers, it would take longer than the lifetime of the universe for an algorithm to factor their product.
But such encryption techniques have their vulnerabilities. Certain products – alled weak keys– happen to be easier to factor than others. Also, Moore’s Law continually ups the processing power of our computers. Even more importantly, mathematicians are constantly developing new algorithms that allow for easier factorization.
Quantum cryptography avoids all these issues. Here, the key is encrypted into a series of photons that get passed between two parties trying to share secret information. The Heisenberg Uncertainty Principle dictates that an adversary can’t look at these photons without changing or destroying them.
“In this case, it doesn’t matter what technology the adversary has, they’ll never be able to break the laws of physics,” said physicist Richard Hughes of Los Alamos National Laboratory in New Mexico, who works on quantum cryptography.
Problems with using Quantum Cryptography
But in practice, quantum cryptography comes with its own load of weaknesses. It was recognized in 2010, for instance, that a hacker could blind a detector with a strong pulse, rendering it unable to see the secret-keeping photons.
Renner points to many other problems. Photons are often generated using a laser tuned to such a low intensity that it’s producing one single photon at a time. There is a certain probability that the laser will make a photon encoded with your secret information and then a second photon with that same information. In this case, all an enemy has to do is steal that second photon and they could gain access to your data while you’d be none the wiser.
Alternatively, noticing when a single photon has arrived can be tricky. Detectors might not register that a particle has hit them, making you think that your system has been hacked when it’s really quite secure.
“If we had better control over quantum systems than we have with today’s technology” then perhaps quantum cryptography could be less susceptible to problems, said Renner. But such advances are at least 10 years away.
Still, he added, no system is 100 percent perfect and even more advanced technology will always deviate from theory in some ways. A clever hacker will always find a way to exploit such security holes.
Any encryption method will only be as secure as the humans running it, added Hughes. Whenever someone claims that a particular technology “is fundamentally unbreakable, people will say that’s snake oil,” he said. “Nothing is unbreakable.”
This text is also published in Ahmed Banafa’s LinkedIn profile
Ahmed Banafa, Author the Books:
Secure and Smart Internet of Things (IoT) Using Blockchain and AI
Blockchain Technology and Applications
References:
http://www.qi.damtp.cam.ac.uk/node/38
http://www.businessinsider.com/what-is-quantum-encryption-2014-3#ixzz33jYuMw48
http://www.wired.com/2013/06/quantum-cryptography-hack/
http://searchsecurity.techtarget.com/definition/quantum-cryptography
http://science.howstuffworks.com/science-vs-myth/everyday-myths/quantum-cryptology.htm
http://www.wisegeek.com/what-is-quantum-cryptography.htm
http://www.techrepublic.com/blog/it-security/how-quantum-cryptography-works-and-by-the-way-its-breakable/
Comments on this publication