The iris scanner found in the Samsung Galaxy 8 is an example of a security tool based on facial recognition, a different version of which has also been integrated into the new iPhone X—recently introduced by Apple—in the Face ID feature. Facial recognition technology, first developed in the 1960s, has become the big star of biometrics in smartphones. Until now it has been used primarily by government agencies and high-security companies, although industry experts expect the Apple effect to popularize the method—as it did with fingerprint sensors—on mobile and home devices.

The question that arises is whether this tool is safe. If you use a fingerprint-unlock system, the likelihood of someone else accessing your device is one in 50,000, according to Phil Schiller, Apple’s vice president of product marketing. “With facial recognition, the possibility is one in a million,” he says.
A 3D map of the face
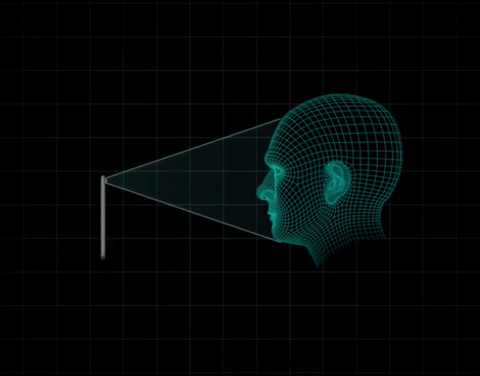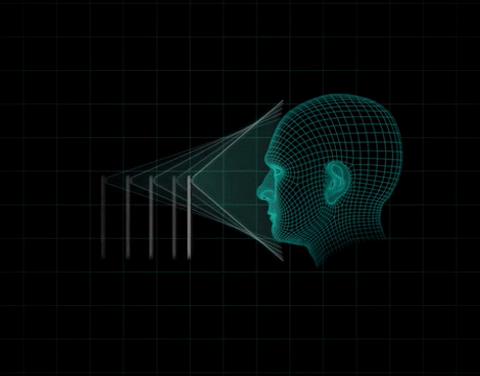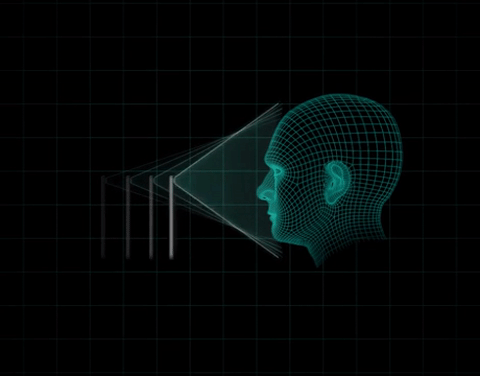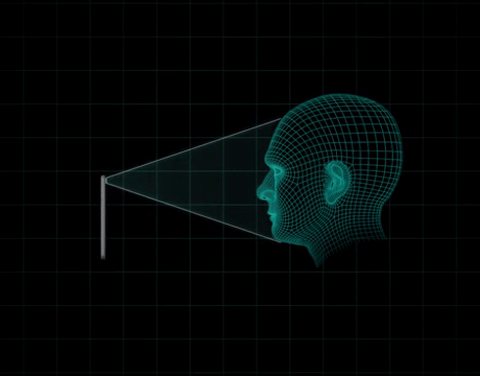
Face ID uses a front camera with an ambient light sensor and an infrared illumination system (that allows a user to be identified even in the dark) coupled with facial recognition software. The system illuminates the scene, detects the user’s face and maps 30,000 infrared points to create a model of mathematical patterns between the different distances and depths of the individual’s face and thereby generate the identification.
The result is a kind of map in three dimensions that is transformed into a mathematical model stored in an encrypted way on the phone. When the system detects that the face matches the previously generated model, it unlocks the terminal. Apple claims that thanks to the neural networks of automatic learning that operate on the iPhone X, the device is able to detect changes in the user’s face over time and modify the first model. Wearing accessories such as glasses or hats or changing the cut or color of the hair does not alter the effectiveness of the system, the company asserts.
“A face is much more unique than a fingerprint, from the perspective of acquiring data about an individual. There is a vast amount of information that a standard front camera can collect—data on the nose, mouth, chin… And when you calculate the relationship between each feature, you have a more reliable recognition map,” explains to Open Mind John Wojewidka, director of business development at FaceTec.
The advantages over the fingerprint
His start-up has created the ZoomLogin technology, a facial recognition system with a tactic different from that of the iPhone—it collects several frames and then observes how the measurements of some facial features, such as the tip of the nose, for example, change as the user moves the phone towards their face. The app compares that distortion with images already stored on the phone’s camera to identify the owner of the smartphone.
Wojewidka points out that the fingerprint is an “excellent way” to open a device, but it is not a security feature. “There are some kinds of fingerprint formats that are common among many people, and without a 100% complete digital fingerprint image, there is probably another that is similar enough to the original.”
Another obstacle is that fingerprint readers can perform poorly if the fingers are dirty, greasy or wet, or when the weather is too cold or a person’s fingerprints have been worn down by years of manual labor or an accident. “In addition, fingerprints can be purchased and reproduced from different sources, such as a high-resolution photograph. A hacker could turn them into a latex representation and use them in a typical reader to gain access,” Wojewidka adds. A famous case occurred in 2014, when the German Defense Minister, Ursula von der Leyen, had her fingerprints hacked from a high-resolution photograph.
Problems with twins and minors
Facial recognition has its own obstacles. The technology is unable to distinguish between identical twins. In those cases (and for adolescents under the age of thirteen, whose facial features may not yet have fully developed), Apple recommends that users employ a password as an extra security measure.
Another threat is the use of 3-D masks. Experts at the CyLab Biometric Center at Carnegie Mellon University point out to Open Mind that while FaceTec software can prevent forgery attempts through videos or user photographs, it would probably not work with a 3-D mask. Apple claims to have trained Face ID to recognize that specific type of falsification. Experts also warn that software-based face recognition systems would require “additional hardware protection to match the security level of Face ID technology.”

Despite the security breaches, the future is biometric. The prediction is that mobile devices will combine sensors for the voice, iris, face and fingerprints. “Biometrics will be an alternative in Multifactor Authentication (MFA) stacks, mixing passwords, PINs, face recognition and other technologies,” says Wojewidka. But he points out that multifactor systems can also have breaches. In other words, your safety will depend on the methods you integrate. “So if the tools of that stack are weak, there is no real security,” admits Wojewidka.
Comments on this publication